Blockchain Technology Security: Strengths and Vulnerabilities

Blockchain security is the collection of tools and mechanisms used to protect digital information from hackers and cyber threats.
On this page
Cyber risks grow and take new forms as technology evolves. Criminals are increasingly using AI to hack both traditional data systems and blockchain networks through phishing emails, fake airdrops, malware attacks, and other methods.
At the same time, the fast progress of quantum computing introduces new cybersecurity threats, raising concerns about the ability to break existing encryption algorithms. But legacy systems and blockchains each have their own ways of fighting back against attacks.
In this article, we’ll take a closer look at how blockchain security works, what challenges it faces, and how it differs from traditional IT cybersecurity.
What Is Blockchain Security?
Blockchain technology is one of the options for storing and protecting data. While there are common principles that define how blockchains work, each network relies on its own tools and mechanisms that shape its security level.
Blockchain security is a combination of technologies, rules, and practices that protect blockchain networks from attacks, fraud, and unauthorized access. It covers everything from how data is encrypted and stored to how transactions are verified and who gets access to what information.
Compared to traditional data storage, which relies on a central server or database administrator to manage data, blockchains are decentralized. Traditional systems typically use antivirus software and firewalls to prevent or detect malicious activity. Blockchains, on the other hand, store data across a distributed network of multiple computers and rely on cryptographic techniques to secure it.
Blockchain in cybersecurity has been gaining a larger role in the broader data security industry, thanks to technological features and the rapid growth of the crypto market, which relies on blockchain as its core tech.
What Makes Blockchain Secure
Blockchain has become a go-to technology for protecting data in areas where trust and transparency are essential, like financial records, intellectual property, and supply chains. Its key features, decentralization and transparency, reduce the need to rely on a single authority and make the data harder to mess with. Several key concepts form the foundation of blockchain technology security.
- Immutability. Once data is written to the blockchain, it can’t be changed or deleted. This makes it incredibly difficult for anyone to alter past records or cover up fraudulent activity.
- Decentralization. Instead of relying on a single server or authority, blockchain runs on a network of independent nodes. This removes single points of failure and makes the system harder to attack or take down.
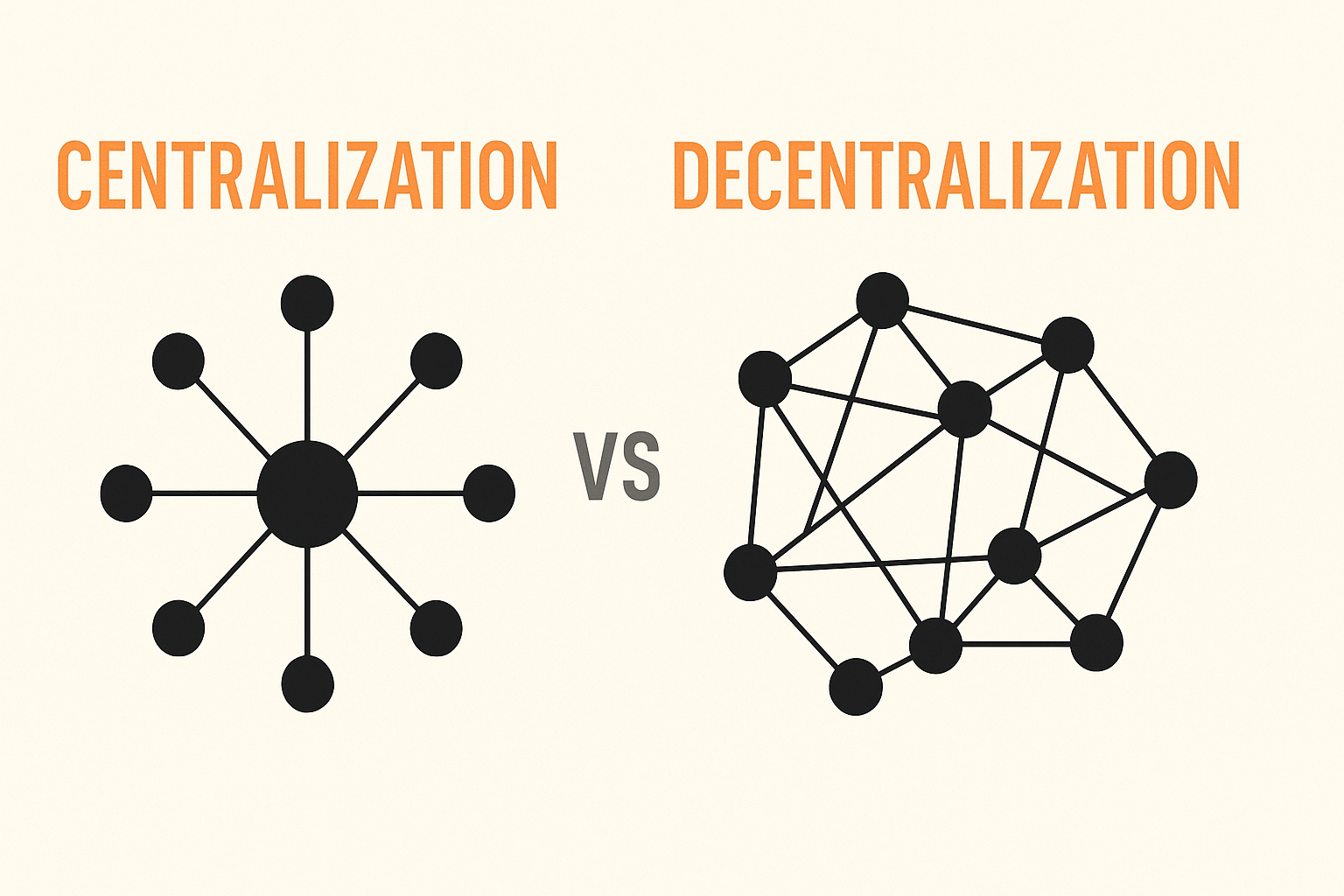
- Transparency and traceability. All transactions are recorded on a public ledger (or a shared ledger in private blockchains), making it possible to track the flow of data or assets from start to finish. This adds visibility and reduces opportunities for manipulation.
- Consensus mechanisms. Blockchain uses special rules, like Proof-of-Work or Proof-of-Stake, to help all computers in the system (called nodes) agree on which transactions are valid. This shared agreement process makes sure no one can add fake data unless most of the network approves it.
- Cryptographic techniques. Advanced encryption methods protect the data on the blockchain. Users sign transactions with private keys, ensuring that only the rightful owner can approve actions tied to their identity or assets.
Despite these benefits, blockchain safety isn’t guaranteed; networks can still be vulnerable to attacks, especially if they’re small or poorly maintained. Not all systems offer the same level of protection. It depends on many factors, including how large and active the network is. For example, the Bitcoin and Ethereum networks are considered highly secure because they have thousands of nodes and a long history of activity.
Blockchain Types
Blockchains come in two main types: public and private. Both use the same core tech: distributed ledgers, cryptographic security, consensus protocols, but they serve different purposes.
Public Blockchains
Transactions on public blockchains, like Bitcoin and Ethereum, can be viewed by everyone through blockchain explorers. Also, anyone can join the network to validate transactions and keep the system running. No one owns the system. Mass participation provides higher security: the more nodes, the harder it is to break the network. You’d need insane computing power to pull off an attack. So, in terms of blockchain cyber security, public chains are very resilient, but they can be slower and use more energy.
Private Blockchains
Unlike public blockchains, private blockchains are controlled by specific organizations or groups. Access is limited to approved users only. This makes them faster and easier to manage, which is why businesses use them for things like supply chains or internal data sharing. Private blockchains focus more on controlling who can see and change data. These systems are typically used within companies and institutions where speed, privacy, and efficiency are prioritized over full decentralization.
Some blockchains are designed to offer a dual approach, allowing for both public and private features within the same network or application. These are often referred to as hybrid or consortium blockchains, which give organizations more flexibility depending on their needs.
Blockchain Attack Types
Crypto criminals are constantly on the lookout for vulnerabilities to exploit blockchain networks, steal funds, scam investors, and carry out other illicit activities. Understanding the different types of attacks can help reduce on-chain risks. Below are some of the most common blockchain attack types:
Routing Attacks
A routing attack targets the internet infrastructure behind blockchain networks, intercepting or manipulating traffic. One common method is a BGP (Border Gateway Protocol) hijack, where attackers trick internet routers into sending blockchain traffic through malicious paths. In 2018, MyEtherWallet (MEW) users lost funds when a BGP hijack redirected traffic bound for Amazon’s DNS (Domain Name System) to a fake site, stealing around $150,000 worth of ETH.
Services like exchanges, mobile wallets, and validator nodes are most vulnerable because they depend on real-time data. Smaller blockchains are also at greater risk due to fewer nodes, while launching a routing attack on a large network like Bitcoin is impractical thanks to its size and decentralization. Routing attacks are hard to detect since they don’t target the blockchain directly but the internet layer. Still, blockchain data security can be improved by encrypting node communication, spreading infrastructure across regions, and actively monitoring for suspicious routing changes.
Phishing Attacks
Crypto phishing attacks are scams where cybercriminals trick users into handing over sensitive information like private keys, seed phrases, or login credentials. They usually show up as fake websites, emails, or DMs that look almost identical to the real thing. And they’re getting smarter. According to Bitget’s 2025 report, AI-generated deepfakes were behind 40% of high-value phishing scams, with $4.6 billion lost in 2024 alone. These scams now include AI-cloned voices and videos that look and sound just like real people, support agents, influencers, or even CEOs. Phishing scams often go viral during high-traffic moments in the crypto space, including airdrops, conferences, and new token listings.
51% Attacks
For a blockchain transaction to be confirmed, most of the network needs to agree that it’s valid. This consensus is what keeps the system secure and trustworthy. If cybercriminals gain control of more than half of the network’s power, they can approve whatever they like, changing recent transactions, stopping other people’s transactions from going through, or spending the same coins twice. 51% attacks are more likely on smaller or newer blockchains that don’t have enough participants to keep the network secure. In contrast, networks like Bitcoin and Ethereum are highly decentralized, making this kind of attack extremely difficult and expensive to pull off. To prevent 51% attacks, blockchain networks rely on strong consensus rules, a large and active validator base, and economic incentives that make attacking the network less profitable than playing by the rules.
Bridge Attacks
Bridges are essential for moving assets between different blockchains, like sending tokens from Ethereum to Solana. The compromise of a bridge can affect the stability and trust in multiple DeFi projects that rely on it for cross-chain liquidity. By hacking bridges, criminals can drain large amounts of cryptocurrency from the bridge’s reserves, move illicit funds from one blockchain to another, devalue a specific asset on one platform but not others, and other malicious activities. Bridges are popular targets for hackers. A major example is the Ronin Bridge hack in 2022, where attackers stole $540 million by taking control of validator nodes.
Rug Pull Schemes
A rug pull is a type of crypto scam where the team behind a token suddenly abandons the project, taking all the money investors put in. This kind of exit scam often follows a predictable pattern: someone launches a token, hypes it up online, attracts investors, and then suddenly cashes out. These scams are especially common in memecoins, as they tend to go viral quickly.
One of the most high-profile rug pull accusations involves Hailey Welch, better known as the “Hawk Tuah” girl. She launched a token called $HAWK in December 2024, which quickly gained attention and surged in value until heavy sell-offs caused it to crash. Wallets linked to the project reportedly walked away with millions, sparking accusations of fraud and leaving many investors at a loss.
To avoid falling for a crypto rug pull, always research the project thoroughly, check the credibility of the team, review the tokenomics, and be cautious of hype with no real product or long-term vision.
Blockchain Network Security: Know the Risks
Blockchain technology offers strong security features, but it’s not immune to attacks. Criminals exploit user mistakes, target bridges between networks, and manipulate smaller blockchains.
Security depends on network size, proper implementation, and user behavior. Large networks like Bitcoin and Ethereum offer better protection than smaller chains. Private keys remain the weakest link; lose them, and no amount of blockchain security matters.
The key is to know the risks, use trusted networks, follow simple safety rules, double-check what you’re doing, and never share your private info with anyone.
The information published on CoinRevolution is intended solely for general knowledge and should not be considered financial advice.
While we aim to keep our content accurate and current, we make no warranties regarding its completeness, reliability, or precision. CoinRevolution bears no responsibility for any losses, errors, or decisions made based on the material provided. Always do your own research before making financial choices, and consult with a qualified professional. For more details, refer to our Terms of Use, Privacy Policy, and Disclaimers.